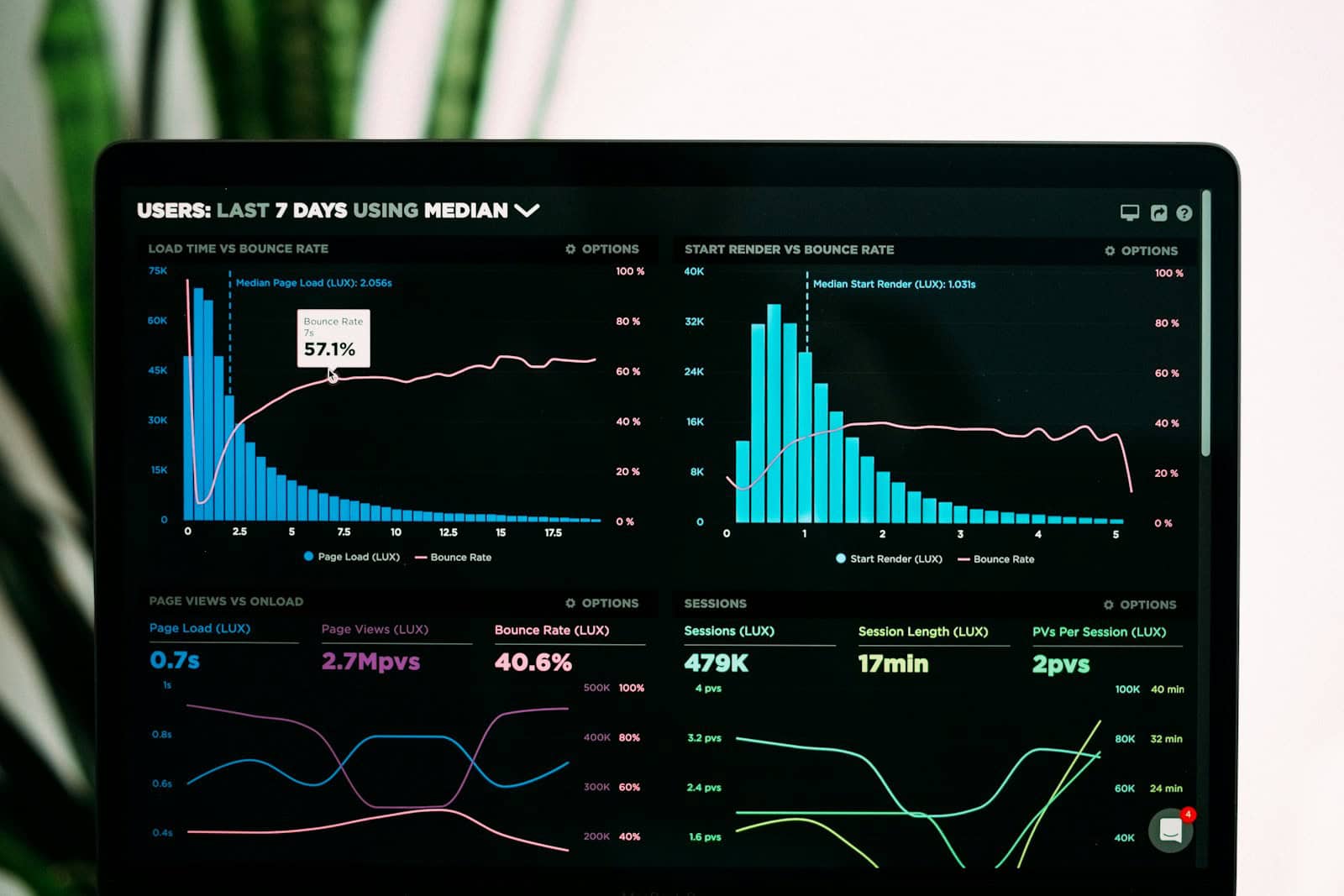
Have you ever wondered how your text messages, emails, or videos travel across the internet? The internet moves data from one place to another using a system that breaks information into small pieces. When you send or receive data online, it’s translated into bits—pulses of light or electricity—that travel through cables, fiber optics, or wireless signals across a vast network of connected devices.
These bits don’t travel as one big chunk. Instead, they’re split into smaller packages called packets. Each packet contains part of your data along with information about where it came from and where it’s going. This method, called packet switching, allows many users to share the same network paths at once, making the internet efficient.
The packets travel through various network devices like routers and switches before reaching their destination. Once there, they’re reassembled into their original form. This whole process happens in milliseconds, making it seem instant to us. Different protocols like HTTP, FTP, and TCP/IP work together to make sure your data gets where it needs to go correctly.
A Technical Look At How Data Is Transmitted On The Internet
The internet is often thought of as a cloud where data magically travels from one place to another. In reality, data transmission on the internet is a complex, highly coordinated process involving physical hardware, networking protocols, and data structures. Here’s a technical breakdown of how data gets from point A to point B over the internet.

1. Data Transmission Starts With Digitization
Everything on the internet—emails, videos, websites—exists as digital data. This data is converted into binary code, a series of 1s and 0s that represent information in electronic form. When you send or request data, your device (computer, phone, tablet) translates your action into this digital format.
2. Data Packets: The Fundamental Units of Transmission
Rather than sending large files all at once, data is broken down into small pieces called packets. Each packet typically contains:
- Header: Includes routing information, such as source and destination IP addresses.
- Payload: The actual chunk of data being sent (part of an email, video, etc.).
- Footer (or trailer): Contains error-checking data like checksums.
This packet-based system ensures reliable, efficient data transfer, even over congested or unreliable networks.
3. OSI and TCP/IP Models: Layered Communication Protocols
The process of transmitting data follows a layered architecture. Two widely referenced models are:
- OSI Model: Conceptual framework with 7 layers (Physical, Data Link, Network, Transport, Session, Presentation, Application).
- TCP/IP Model: Practical implementation with 4 layers (Link, Internet, Transport, Application).
Each layer handles specific functions:
- Application Layer: Where protocols like HTTP, FTP, and SMTP operate.
- Transport Layer: Ensures reliable transmission via TCP (Transmission Control Protocol) or faster, less reliable delivery via UDP (User Datagram Protocol).
- Internet Layer: Handles addressing and routing via IP (Internet Protocol).
- Link Layer: Controls physical transmission over Ethernet, Wi-Fi, fiber optics, etc.
4. The Journey of Data: From Device to Server (And Back)
Step 1: From Device to Router
- Data packets are sent from your device to your router, usually over Wi-Fi or Ethernet.
- The router adds the next-hop information and forwards the packets.
Step 2: Router to ISP (Internet Service Provider)
- Your home router connects to your ISP through a modem.
- The ISP acts as a gateway to the wider internet, determining how to route your packets.
Step 3: Traversing the Internet Backbone
- Packets move across internet exchange points (IXPs) and data centers, hopping through routers and switches operated by different ISPs and network providers.
- Protocols like BGP (Border Gateway Protocol) direct packets across multiple autonomous systems (AS), ensuring they take efficient routes.
Step 4: Reaching the Destination Server
- After crossing multiple networks, the packets arrive at the destination server, where the requested data resides (like a web page or video).
Step 5: Return Path
- The server responds by sending data back in the form of packets, following a similar route in reverse (though not necessarily the same exact path).
5. How Data Integrity and Reliability Are Maintained
- TCP Protocol: Ensures reliable transmission with packet sequencing, acknowledgments (ACKs), and retransmissions if packets are lost or arrive out of order.
- Checksums and CRC (Cyclic Redundancy Check): Detect data corruption within packets.
- Flow Control and Congestion Control: Manage network traffic to avoid overwhelming the recipient or the network.
6. Physical Transmission Mediums
Data travels over various mediums:
- Copper Wires (DSL, Ethernet): Use electrical signals.
- Fiber Optic Cables: Transmit data as pulses of light, allowing ultra-high-speed transmission over long distances.
- Wireless (Wi-Fi, Cellular): Use radio waves for last-mile delivery.
Undersea fiber optic cables form the global backbone of the internet, carrying the majority of international data traffic.

7. DNS: Translating Domain Names to IP Addresses
When you type a URL (like www.example.com), your request goes through a DNS (Domain Name System) lookup:
- DNS servers translate the domain into an IP address the network can use to route your request.
- This IP address is included in your data packets to direct them to the correct server.
8. Encryption and Security
- HTTPS (SSL/TLS) encrypts data between your browser and the web server to protect privacy.
- VPNs (Virtual Private Networks) create encrypted tunnels for secure data transmission, masking your IP address and location.
- Firewalls and Intrusion Detection Systems (IDS) monitor and protect data packets from malicious interference.
9. Latency and Bandwidth Considerations
- Latency: The time it takes for data to travel from source to destination. Measured in milliseconds (ms).
- Bandwidth: The maximum data transfer capacity of a network, typically measured in Mbps or Gbps.
Both affect the speed and quality of data transmission, influencing streaming, gaming, and web browsing experiences.
Data transmission on the internet is a highly orchestrated process combining hardware infrastructure, routing protocols, data encapsulation, and error correction—all working together to ensure data gets from one place to another securely and efficiently.
Key Takeaways
- Internet data travels as electrical or light pulses (bits) through physical infrastructure like cables and wireless networks.
- Data is broken into small packets that can take different routes to reach the same destination, making transmission reliable and efficient.
- Network protocols ensure data packets are properly sent, received, and reassembled at their destination.
Understanding Data Transmission on the Internet
Data transmission on the internet involves moving information from one device to another through various physical mediums and following specific rules called protocols. This complex process happens in milliseconds, allowing us to share everything from text messages to streaming videos.
Basic Concepts of Data Transmission
Data transmission starts when information is broken into smaller units called packets. These packets travel independently through the internet, often taking different routes to reach the same destination. Think of packets like envelopes in the mail system – each contains part of a message and information about where it’s going.
The physical transport of data happens through different mediums. These include:
- Copper wires: Using electrical signals
- Fiber optic cables: Using light pulses
- Wireless signals: Using radio waves
Data moves through these channels at different speeds. Fiber optic cables are fastest, transmitting data at nearly the speed of light. Copper wires are slower but still widely used. Wireless transmission varies in speed based on signal strength and interference.
The Role of Protocols in Data Transmission
Protocols are sets of rules that govern how data is sent, received, and processed. They ensure devices can communicate regardless of their manufacturer or operating system.
The most important protocols include:
TCP/IP (Transmission Control Protocol/Internet Protocol) – This pair forms the foundation of internet communication. IP handles addressing and routing packets to their destination. TCP ensures all packets arrive correctly and in the right order.
HTTP/HTTPS manages how web browsers and servers exchange information. HTTPS adds encryption for security.
DNS (Domain Name System) translates human-readable website names into IP addresses that computers understand.
Without these protocols, the internet couldn’t function. They provide the common language that allows billions of devices to communicate efficiently across vast networks.
Data Packets and Packet Switching
The internet transmits information by breaking it into small pieces called data packets and sending them through a network using packet switching. This method allows for efficient, reliable data transfer across the global internet infrastructure.
Structure of Data Packets
Data packets are small chunks of information that travel across the internet. Each packet contains two main parts: the header and the payload. The header works like an envelope, holding important details such as:
- Source IP address (where the packet came from)
- Destination IP address (where it’s going)
- Sequence number (packet order in the complete message)
- Time-to-live value (how long the packet can exist)
The payload carries the actual data being sent, such as part of an email, video, or website content. Packets typically range from 1,000 to 1,500 bytes in size.
Network devices use framing to identify where packets begin and end. This framing adds special markers that help routers and switches process each packet correctly.
How Packet Switching Works
Packet switching moves data across networks by sending individual packets along the most efficient available paths. Unlike older circuit switching methods that required dedicated connections, packet switching allows many users to share network resources simultaneously.
When you send data:
- Your device breaks the data into packets
- Each packet may take different routes to the destination
- Routers examine packet headers to determine the best path forward
- Packets travel through multiple network devices before reaching their destination
- The receiving device reassembles the packets into the original data
This method offers several advantages. If one path becomes congested or fails, routers can redirect packets through alternative routes. Network resources are used more efficiently since multiple communications can share the same connections.
Packet switching forms the foundation of the Internet Protocol (IP), which enables devices worldwide to communicate regardless of their hardware or software differences.
Internet Protocols and Their Functions
Internet protocols are sets of rules that govern data exchange on the internet. They define how data is formatted, transmitted, received, and processed across different networks.
Transmission Control Protocol (TCP)
TCP ensures reliable data transmission between devices. It breaks data into packets and guarantees they arrive complete and in order. When you send an email or download a file, TCP checks that all information reaches its destination correctly.
TCP works by establishing a connection between two devices before data transfer begins. This connection setup involves a “three-way handshake,” where devices exchange messages to confirm they’re ready to communicate.
If a packet gets lost during transmission, TCP detects this through checksums and acknowledgments. The sending device will automatically resend any missing packets. This reliability makes TCP crucial for applications where data accuracy matters more than speed.
TCP assigns port numbers to different applications on your device. For example, web browsers typically use port 80 or 443, while email uses ports 25 or 587.
Internet Protocol (IP)
IP handles the addressing and routing that gets data from one computer to another across networks. It assigns each device a unique IP address, similar to a home address for mail delivery.
There are two main versions of IP in use today: IPv4 and IPv6. IPv4 uses 32-bit addresses (like 192.168.1.1), while IPv6 uses 128-bit addresses to solve the problem of address exhaustion.
IP works by adding a header to each data packet. This header contains:
- Source IP address
- Destination IP address
- Protocol information
- Packet sequencing data
IP doesn’t guarantee delivery or check if packets arrive in order. It simply routes packets to their destination along the best path available. This “best effort” approach makes IP fast but unreliable without TCP’s help.
TCP/IP Suite
The TCP/IP suite combines multiple protocols that work together in layers. This model defines how data moves from one device to another on the internet.
The four main layers of the TCP/IP model are:
- Network Interface Layer: Handles physical connection to the network
- Internet Layer: Routes packets using IP
- Transport Layer: Manages data flow with TCP or UDP
- Application Layer: Supports specific applications like HTTP or FTP
This layered approach allows each protocol to focus on a specific task. When you browse a website, your request travels down through these layers, across the internet, and back up through the layers on the web server.
The TCP/IP suite forms the foundation of internet communication. Nearly all internet services rely on these protocols to function.
Other Relevant Protocols
User Datagram Protocol (UDP) provides a faster but less reliable alternative to TCP. It doesn’t establish connections or confirm delivery, making it ideal for streaming media, online gaming, and other time-sensitive applications.
Hypertext Transfer Protocol (HTTP) defines how web browsers and servers communicate. It’s the backbone of the World Wide Web, transferring webpage content to your browser.
Domain Name System (DNS) translates human-readable website names (like google.com) into IP addresses computers can use. Without DNS, you’d need to memorize IP addresses instead of website names.
File Transfer Protocol (FTP) enables file uploads and downloads between computers. Though older, it remains important for website management and data sharing.
Simple Mail Transfer Protocol (SMTP), Post Office Protocol (POP3), and Internet Message Access Protocol (IMAP) work together to send, receive, and store email.
Network Infrastructure
Network infrastructure forms the backbone of internet data transmission. It consists of physical components and devices that allow computers to connect and share information across networks.
Servers and Clients
Servers are powerful computers that store websites, files, and applications. They respond to requests from client devices like laptops, smartphones, and tablets. When you type a website address, your client device asks a server to send the website data.
Servers typically have more processing power and memory than regular computers. They run special software that manages multiple connections at once. Many large websites use multiple servers to handle high traffic.
Client devices initiate connections to servers. Your home computer, phone, or smart TV are all client devices. They request data, process it, and display it for users.
This client-server relationship is fundamental to how the internet works. Clients ask for information, and servers provide it.
Networking Hardware
Routers direct data packets to their correct destinations. They act like traffic cops, checking each packet’s IP address and deciding the best path forward. Without routers, data couldn’t find its way through the complex internet.
Modems convert digital signals from your computer into signals that can travel over phone lines or cable connections. They serve as translators between your home network and your internet provider.
Switches connect multiple devices within a local network. Unlike routers, they only forward data to specific devices, not between networks.
Network cables provide the physical connections. These include:
- Copper cables: Ethernet cables that use electrical signals
- Fiber optic cables: Use light pulses to transmit data at very high speeds
- Wireless connections: Use radio waves to connect devices without physical cables
Transmission Reliability and Control
The internet moves data across vast networks with critical mechanisms to ensure reliability. These systems handle packet loss, maintain order, and guarantee data quality, all while meeting performance requirements.
Ensuring Data Integrity
Data integrity is vital when transmitting information across networks. TCP (Transmission Control Protocol) plays a key role by breaking messages into packets and tracking which ones have been received. When packets are lost or corrupted, TCP requests retransmission.
Error detection methods like checksums and CRC (Cyclic Redundancy Check) verify data hasn’t changed during transmission. A checksum adds the values of data and sends this sum along with the original data. The receiver calculates its own sum and compares the two.
CRC offers stronger protection than simple checksums. It uses polynomial division to create a value that detects both single and burst errors in transmission.
Unlike TCP, UDP (User Datagram Protocol) provides faster but less reliable transmission. It lacks the error-checking mechanisms of TCP, making it suitable for applications where speed matters more than perfect delivery, such as live streaming.
Quality of Service and SLA
Quality of Service (QoS) settings prioritize certain types of network traffic. This ensures critical applications receive bandwidth when networks become congested. Video calls, for example, need consistent data flow to avoid freezing or audio problems.
Networks implement QoS through:
- Traffic shaping – Controls flow rates
- Packet classification – Identifies traffic types
- Packet scheduling – Determines transmission order
Service Level Agreements (SLAs) establish guaranteed performance metrics between providers and users. These contracts specify minimum standards for:
- Uptime percentage (often 99.9% or higher)
- Maximum latency (delay)
- Packet loss rates
- Response times for outages
For streaming services, SLAs might guarantee sufficient bandwidth to prevent buffering. Financial institutions might require extremely low latency for trading applications where milliseconds matter.
Bandwidth and Data Flow
Bandwidth plays a crucial role in determining how quickly data travels across the internet. It directly affects the user experience for everything from basic web browsing to high-definition streaming.
Measuring Bandwidth
Bandwidth refers to the maximum capacity of a network connection to transmit data in a given amount of time. It’s typically measured in bits per second (bps) or more commonly in megabits per second (Mbps) or gigabits per second (Gbps) for faster connections.
Different connection types offer varying bandwidth capabilities:
- Dial-up: 56 Kbps
- DSL: 1-100 Mbps
- Cable: 10-500 Mbps
- Fiber optic: 250-1000+ Mbps
Network administrators use specialized tools to measure actual bandwidth performance. These tools analyze the rate at which data packets move through specific network segments.
This measurement helps identify bottlenecks where data flow slows down. For home users, simple speed tests can provide a rough estimate of available bandwidth.
Impact on Data Transfer Rates
Higher bandwidth allows more data to flow simultaneously, significantly improving transmission speeds. When streaming video, for example, more bandwidth means higher resolution without buffering interruptions.
Bandwidth limitations can create congestion points in networks. This is particularly noticeable during peak usage times when many users access the same services simultaneously.
Services like Netflix or YouTube adjust video quality based on detected bandwidth. They send smaller data packets when bandwidth is limited, reducing quality to maintain smooth playback.
Network communication protocols also adapt to bandwidth availability. They’ll adjust packet sizes and transmission rates to optimize performance under current conditions.
For businesses, sufficient bandwidth ensures critical applications run smoothly. It enables multiple services to operate simultaneously without competing for limited resources.
Data Sharing and Services
The internet connects countless devices, enabling the exchange of files, messages, and other digital content. This connection powers countless services that have become essential to our daily lives.
Data Sharing Between Users
Data sharing is the process of making data available to multiple users and applications. When you send a message or file to someone, your device converts this information into packets that travel through various networks to reach the recipient.
Files can be shared through email attachments, cloud storage platforms, or direct messaging apps. These methods use different protocols to ensure your data arrives intact and securely.
Most modern sharing happens through client-server models. Your device (the client) connects to a server that processes and routes your data to its destination. Internet Service Providers (ISPs) play a crucial role by maintaining the infrastructure that carries these data packets.
Security is vital in data sharing. Encryption transforms your information into code that only the intended recipient can unlock, protecting private data from unauthorized access.
Internet Services
Internet services are applications that use data transmission to provide specific functions to users. These services rely on servers that store information and respond to requests from client devices.
Common services include:
- Web browsing: Loading websites from servers to your device
- Email: Sending and receiving messages through mail servers
- Video streaming: Delivering video content in real-time
- Cloud storage: Storing files on remote servers for access anywhere
These services use specialized protocols to communicate. For example, websites use HTTP or HTTPS, while email relies on SMTP and POP3/IMAP protocols.
Service providers maintain large data centers with powerful computers that process millions of requests simultaneously. When you use Google or Netflix, your request travels to these centers where it’s processed before a response is sent back to you.
ISPs ensure these connections remain stable, acting as the highway system for all internet traffic between users and services.
Connecting Devices and Networks
Networks connect our devices to the internet through specialized equipment and service providers. These connections form the backbone of how data moves from one place to another across the globe.
Role of Routers and Switches
Routers and switches are key network devices that direct data to its proper destination. Switches connect devices within a local network, like computers in an office. They create pathways that allow these devices to communicate with each other.
Routers work at a higher level by connecting different networks together. When you send data to a website, your router determines the best path for that data to travel. It reads the destination IP address and forwards packets accordingly.
These devices use routing tables to make decisions about where to send information. Think of routers as traffic cops at intersections, directing data packets to the correct roads toward their destinations.
Modern routers also provide security features that protect your network from unwanted access. They create a barrier between your private network and the public internet.
Internet Service Providers (ISPs)
ISPs are companies that connect your home or business network to the wider internet. They maintain the infrastructure needed to transmit data over long distances using fiber optic cables, copper wires, or wireless signals.
When you sign up with an ISP, they provide you with access to their network. This connection serves as your entry point to the internet. ISPs operate at different levels:
- Local ISPs: Serve specific regions or communities
- Regional ISPs: Connect local ISPs together
- Tier-1 providers: Own the major backbone networks spanning continents
Your data travels from your router to your ISP’s network. From there, it may pass through several other ISP networks before reaching its destination. ISPs use various technologies to transmit data, including DSL, cable, fiber optic, and satellite connections. The type of connection affects your internet speed and reliability.
Frequently Asked Questions
Internet data transmission involves several technical processes that work together to move information from one point to another. These processes include various methods of physical transmission, protocols that coordinate data flow, and security measures that protect information.
Which methods are employed for transferring data across the Internet?
Data travels across the Internet through different physical media. These include copper cables (like twisted pair used in many homes), fiber optic cables that use light signals, and wireless transmissions.
Fiber optic cables offer the fastest speeds and can carry data over long distances without signal degradation. They use pulses of light to transfer information through thin glass strands.
Wireless methods include Wi-Fi, cellular networks (4G/5G), and satellite connections. These options provide flexibility but may be affected by physical obstacles or weather conditions.
What roles do protocols play in the transmission of data over the Internet?
Protocols are sets of rules that govern how data is packaged, addressed, transmitted, and received. TCP/IP (Transmission Control Protocol/Internet Protocol) is the foundation of internet communication.
HTTP and HTTPS manage web page requests and delivery. SMTP handles email transmission, while FTP controls file transfers between computers.
These protocols ensure devices from different manufacturers can communicate effectively. They work like a common language that all internet-connected devices understand and follow.
In what ways is data encryption used to secure information transmitted over the Internet?
Encryption transforms data into coded text that can only be read with the correct decryption key. This protects sensitive information like passwords and financial details from being intercepted.
HTTPS uses SSL/TLS encryption to secure website connections. This creates a private “tunnel” for data to travel between your browser and the website server.
VPNs (Virtual Private Networks) encrypt all internet traffic from a device, hiding both the content and destination of data. This adds security when using public Wi-Fi networks.
How does packet switching facilitate data transmission on the Internet?
Packet switching breaks data into small chunks called packets before sending them. Each packet contains the data plus information about its source, destination, and position in the complete message.
This method allows networks to handle multiple communications simultaneously. Packets from different messages can share the same network paths, making efficient use of available bandwidth.
If some packets get lost, only those specific packets need to be resent rather than the entire message. This makes the system more resilient and efficient.
Can you explain the function of routers in directing data traffic online?
Routers act as traffic directors for data packets. They examine the destination address in each packet and determine the best path for it to travel toward its destination.
When you send data over the internet, it typically passes through multiple routers. Each router makes an independent decision about where to send the packet next.
Routers can also prioritize certain types of traffic. For example, video call data might be prioritized over email to ensure smooth communication in real-time applications.
What technologies contribute to locating devices within the Internet’s infrastructure?
IP addresses serve as unique identifiers for all internet-connected devices. IPv4 addresses (like 192.168.1.1) are being supplemented by IPv6 addresses as the number of connected devices grows.
DNS (Domain Name System) converts human-readable website names into IP addresses. This lets users type “example.com” instead of remembering numeric IP addresses.
MAC addresses identify specific hardware devices on a local network. Unlike IP addresses which can change, MAC addresses are permanently assigned to network interfaces during manufacturing.