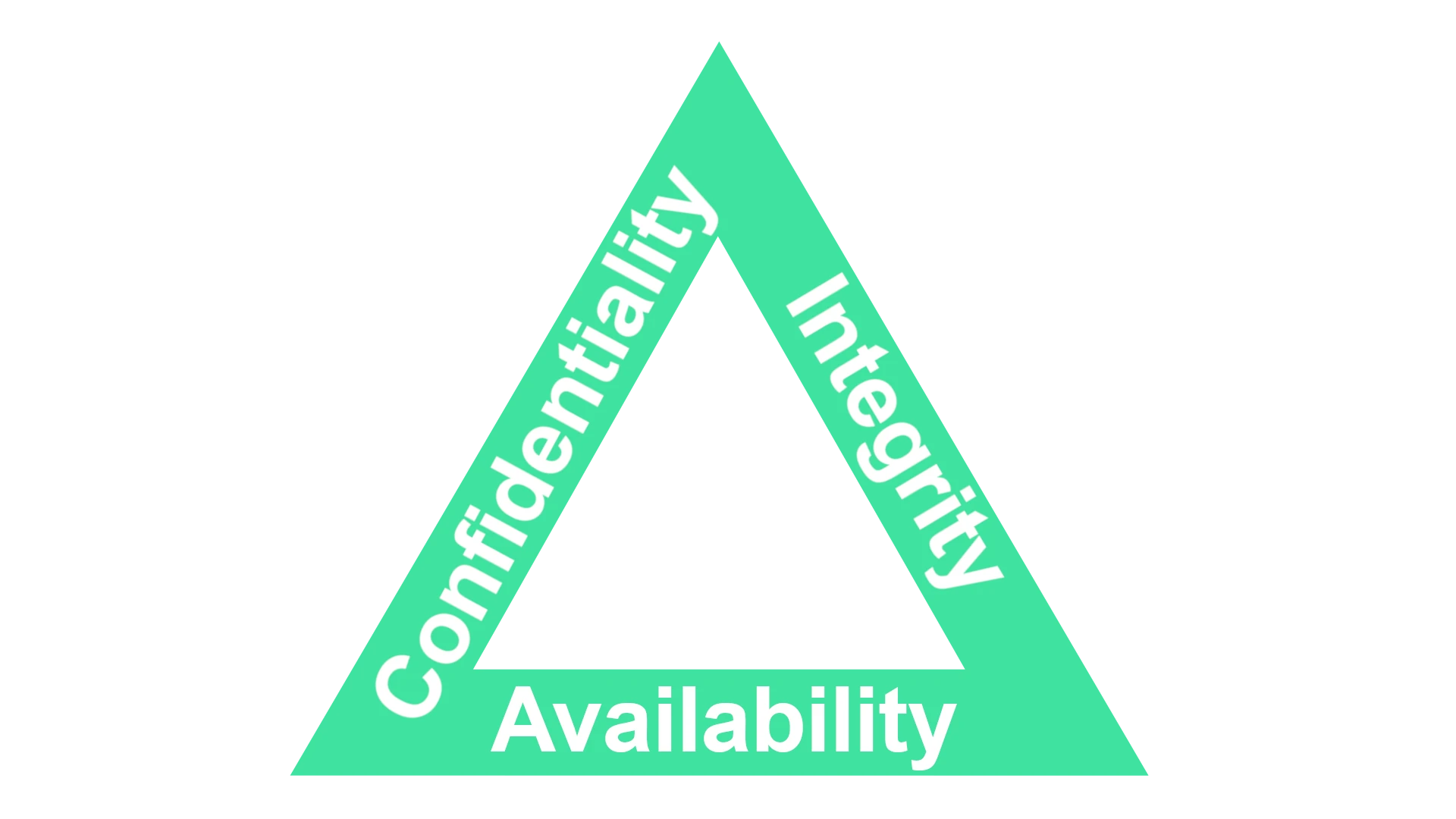
The CIA Triad is a fundamental model that defines the standard for securing information systems. It is essential to maintain a robust defense against the ever-present cyber risks. The model is based on three core principles: confidentiality, integrity, and availability. Confidentiality ensures that information is accessible only to those who are authorized to view it. Integrity means maintaining the accuracy and trustworthiness of data, and availability guarantees that users can reliably access the information or systems they need when necessary.
These three principles form the foundation of an organization’s information security structure. They help identify critical areas that require protection and guide the development of policies and controls to safeguard information assets. By upholding the principles of the CIA Triad, organizations can better protect sensitive information from unauthorized access, alterations, or disruptions. This proactive approach to security builds trust among stakeholders and helps ensure the smooth operation of an organization’s services.
The CIA Triad: Your Guide to Information Security
The CIA Triad is a core model in information security. It stands for Confidentiality, Integrity, and Availability. Let’s break down each of these concepts.
Confidentiality: Shielding Sensitive Data
Confidentiality focuses on keeping sensitive information private. This means preventing unauthorized access, disclosure, or theft of data. Encryption, access controls, and secure communication channels are common tools used to ensure confidentiality.
Integrity: Upholding Data Accuracy
Integrity ensures data remains accurate, consistent, and trustworthy throughout its lifecycle. It safeguards data from unauthorized modification, deletion, or tampering. Data validation, checksums, and version control are some methods to maintain data integrity.
Availability: Ensuring Reliable Access
Availability guarantees that authorized users can access information and systems when needed. This involves protecting against outages, disruptions, or attacks that could hinder access. Redundancy, backups, and disaster recovery plans are crucial for maintaining availability.
The CIA Triad in Action: Real-World Examples
Consider a healthcare scenario where patient records are stored electronically. Confidentiality ensures only authorized personnel can view a patient’s medical history. Integrity ensures the records are accurate and not tampered with. Availability ensures doctors can access the records promptly when needed for diagnosis and treatment.
Why the CIA Triad Matters
The CIA Triad provides a framework for understanding and addressing information security risks. It helps organizations prioritize security measures and create a comprehensive security strategy. By balancing these three principles, organizations can better protect their sensitive data and systems, while ensuring business continuity and maintaining trust with their stakeholders.
Overview
- The CIA Triad is a fundamental model in information security.
- It encompasses Confidentiality, Integrity, and Availability.
- Confidentiality protects sensitive data from unauthorized access.
- Integrity ensures data remains accurate and trustworthy.
- Availability guarantees reliable access to information and systems.
- The CIA Triad provides a framework for developing a comprehensive security strategy.
By understanding the CIA Triad and implementing appropriate security measures, organizations can safeguard their valuable information assets and build a strong foundation for information security.
Key Takeaways
- The CIA Triad is pivotal in safeguarding information systems.
- Confidentiality, integrity, and availability are the triad’s main components.
- These principles help shape robust information security policies.
Core Concepts of the CIA Triad
The CIA Triad is critical for keeping data secure. It helps organizations in crafting policies and defenses against various threats to their information systems.
Protecting Against Data Breaches
To protect against data breaches, it is essential to control who can access sensitive data. Authentication and access controls play a pivotal role. Two-factor authentication and multi-factor authentication employ multiple layers of security, ensuring that only authorized users can view sensitive information.
Ensuring System and Data Integrity
Data integrity means that information remains accurate and untampered. Hashing, digital signatures, and checksums verify that data has not changed. This prevents corruption and ensures that data is reliable.
Maintaining Availability and Recovery
Systems must be robust and data must be reachable when needed. Redundancy and failover procedures keep services running during a power outage or server failure. Regular backups and a solid disaster recovery plan help organizations quickly recover from a data breach or natural disaster.
Addressing Legal and Compliance Aspects
All organizations must meet certain regulatory requirements. Security policies and auditing practices ensure compliance and protect privacy. Adherence to laws and frameworks is not just about legal responsibility but also about maintaining customer trust.
Implementing Security Measures and Controls
A comprehensive security program must include policies and technologies to thwart threats like malware and phishing. Intrusion detection systems, encryption, and regular security training for staff mitigate risks. Proper security measures help defend against both direct attacks and social engineering techniques.